Cybersecurity
The cyber threat landscape is constantly evolving, and the news is filled with stories of the latest organization that has experienced a cyber incident. Whether it is threat actors from nation states, cybercriminals, or insider threats, organizations must proactively address and manage cyber risk, protect their critical assets, and comply with new and evolving cybersecurity laws, regulations, and standards. ASR's Cybersecurity services leverage ASR's expertise and capabilities in cybersecurity, as well as ASR's strategic collaboration with cybersecurity experts at several nationally recognized cybersecurity centers of academic exellence, to assist our customers in effectively managing their cyber risk and protecting themselves from cyber attacks. ASR provides tailored, innovative cybersecurity solutions to meet each of our Government and Commercial customers' unique mission and cybersecurity requirements.
ASR's Approach to Cybersecurity
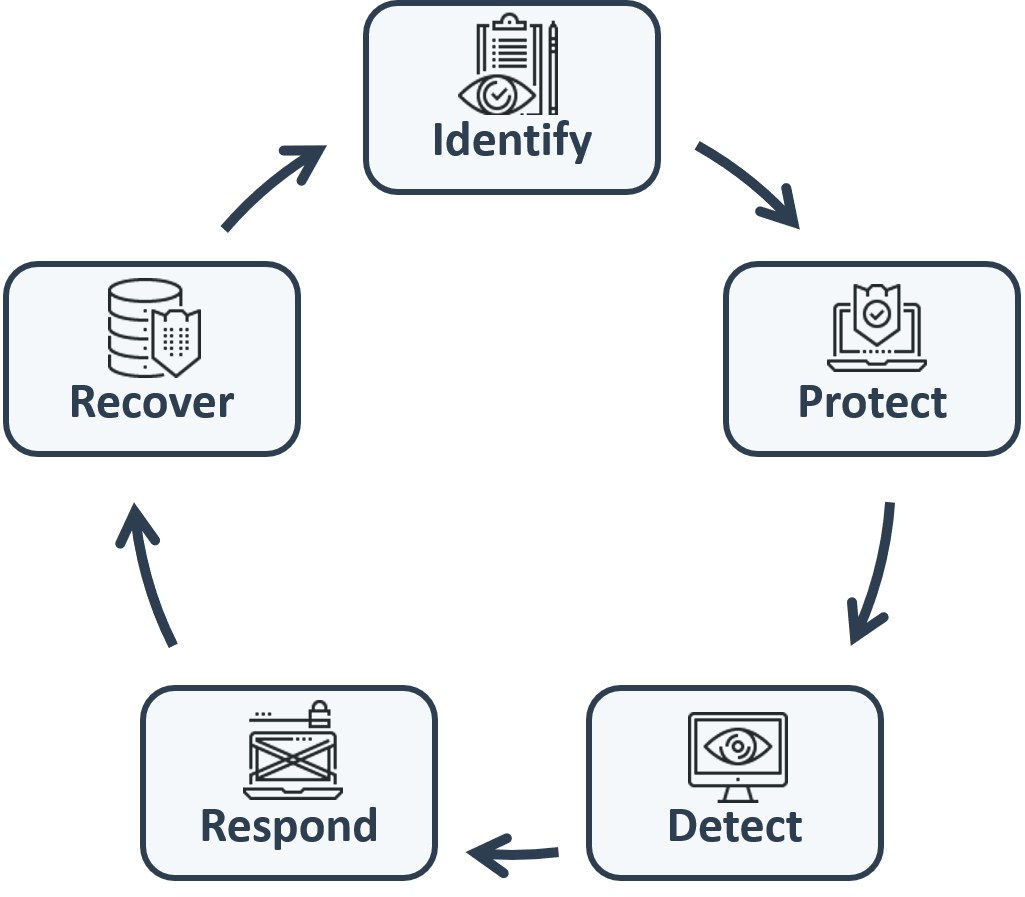
To effectively assist our customers in protecting their critical assets from cyber risk and attack, ASR has developed its approach to effectively leveraging its cybersecurity expertise and capabilities with a focus on the 5 core cybersecurity functions identified by the NIST Cybersecurity Framework.
- 1 Identify - ASR assists our customers in identifying their critical assets, their risks, threats, and vulnerabilities, and applicable cyber laws, regulations, and standards that they must comply with.
- 2 Protect - ASR assists our customers in implementing security governance, policies, processes, procedures, and controls to protect their critical assets from cyber attack and mitigate cyber risk through innovative solutions.
- 3 Detect - ASR assists our customers in detecting anomalous and suspicious cyber activity and cyber threats using the latest in continuous monitoring technology, expertise, and best practices.
- 4 Respond - ASR assists our customers in responding to cyber incidents in an effective manner, minimizing the impact on their organization.
- 5 Recover - ASR assists our customers in recovering from cyber incidents through implementing resilient infrastructure and defenses and developing and executing robust backup, business continuity, and disaster recovery plans and processes.
ASR's Cybersecurity Expertise and Capabilities
Governance, Risk, and Compliance
Effective Cybersecurity programs must align with business objectives and have an effective decision making structure, identify, understand, and manage cyber risks, and understand cyber compliance requirements with laws, regulations, and standards. ASR assists its customers in implementing effective Cyber Governance, Risk, and Compliance strategies, programs, policies, and processes.
- Developing, evaluating, and implementing cybersecurity strategies, governance, plans, policies and processes
- Cybersecurity Governance - Alignment with organizational missions, goals, business processes, planning, implementation, improvements
- Risk Assessment and Management
- Business Impact Analysis (BIA)
- Compliance with Cybersecurity laws, regulations, and standards including RMF, FISMA, FIPS, FedRAMP, RMF, NIST 800-53, NIST 800-171, ISO 27001, DFARS, GDPR, HIPAA
- Categorizing Systems and Selecting Security Controls
- Implementation and Support of Governance, Risk, and Compliance (GRC) Software Solutions
Security Assessment and Authorization
To comply with laws, regulations, and standards, and receive an Authority To Operate (ATO) for IT systems, organizations must document and assess compliance with security controls and effectively assess and mitigate vulnerabilities. ASR's experienced Subject Matter Experts assist our customers in understanding and implementing Assessment and Authorization and Vulnerability Management processes for their critical systems.
- Vulnerability Assessment and Scanning - ACAS, Nessus, SCAP, OpenVAS
- DISA Security Technical Implementation Guide (STIG) Compliance Assessment and Scans
- System Security Plan (SSP) Development Support
- NIST 800-53 Control Assessments
- Penetration Testing
- Risk Management Framework (RMF) Package Development
- Assessment and Authorization (A&A) / Certification and Accreditation (C&A)
- e-MASS Support
- Navy Qualified Validator Support
Cybersecurity Operations and Continuous Monitoring
Effective implementation of technical security controls through secure cybersecurity and IT operations, effective vulnerability management, continuous monitoring to monitor control effectiveness and detect cyber threats, and incident response and recovery are crucial to protecting the confidentiality, integrity, and availability of critical assets. ASR supports and assists our customers with their Cybersecurity Operations and Continuous Monitoring requirements with innovative, cost-effective solutions.
- Computer and Network Defense (CND)
- Endpoint Detection and Response (EDR) Solutions Implementation - Crowd Strike, Carbon Black, Fire Eye, Sophos
- Next Generation Firewalls (NGFW) / Unified Threat Management (UTM) Implementation and Operations - Cisco, Palo Alto, FortiGate
- Access Control / Identity and Access Management
- Backup, Business Continuity, Disaster Recovery
- Security Operations Center (SOC) Support
- Secure Configuration and Asset Management
- Vulnerability and Patch Management
- Continuous Monitoring, Audit, Security Information and Event Management (SIEM) Implementation and Operations
- Incident Response and Recovery
Cybersecurity Engineering
Effectively protecting IT systems and assets from cyber risk and threats depends on incorporating cybersecurity into each phase of the Systems Development Life Cycle (SDLC). ASR's Cybersecurity Engineering support services assist our customers in engineering and implementing effective and cost-efficient secure systems and software applications.
- Security Architecture
- Configuration and Change Management
- Security Automation
- DevSecOps
- Application Security – Secure Software Application Development, Configuration, Data Security
- Implementation of Secure Configuration Baselines (DISA STIGs, USGCB, CIS Benchmarks)
- Secure Network and Infrastructure Design and Implementation
- Implementation of Security Best Practices
Cloud Security
Today, more organizations than ever are undergoing digital transformation and moving their data and applications to the cloud. However, cloud computing presents a unique set of cybersecurity risks, threats, and challenges. ASR assists our customers in securely transforming their organization's IT systems and data to the cloud and understanding and managing the cloud cyber risk.
- Cloud Security Governance
- Developing and implementing cloud security policies, processes, procedures, and controls according to internal and external cloud security governance / standards, including FedRAMP, NIST, ISO, and industry best practices
- Cloud Risk Assessment and Mitigation
- Cloud Vulnerability Assessment and Management
- Cloud Security Engineering & Architecture
- Cloud Application Security
Cybersecurity Program Management Support
The success of an organization's cybersecurity program relies on effective program management, including strategy, planning, performance monitoring, auditing, and resource, budget, and risk management. ASR's Cybersecurity Program Management Support services support our customers wide range of Cybersecurity Program Management support needs with a holistic approach.
- Cybersecurity consulting and advisory services
- Enterprise Cybersecurity Program Management
- Cybersecurity Staffing and Talent Acquisition
- Contract and Acquisition Support
- Communications and Public Relations Support
- Strategy, Policy, and Planning
- Administrative Support
- Process Management
- Cost Management
- Data Analysis and Reporting
Cybersecurity Awareness and Training
People are a key asset in any organization, and are often one of the primary targets by threat actors, often through social engineering attacks. ASR assists organizations in this critical component of their cybersecurity programs by helping organizations provide effective and continuing cybersecurity awareness and training in response to an evolving cyber threat landscape.
- Cybersecurity Training Curriculum and Course Development
- Cyber Awareness, Cyber Hygiene, Threats, Role Based, Best Practices, Social Engineering, Phishing, Incident Response, Insider Threat, Ransomware
- Cybersecurity Training Delivery - Classroom, Online, Audio, Video, Self-Paced
- Cybersecurity Program Development and Management
- Training Effectiveness Assessments and Testing
- ASR Training and Orientation Portal (TOP) - ASR's web platform for online training delivery
Supply Chain Cybersecurity
An organization is only as secure as the weakest link in its supply chain. Threat actors are increasingly attacking vulnerabilities in suppliers, sub-tier suppliers, and third party service providers to compromise organizations. ASR leverages its extensive Supply Chain Management experience across a wide range of industries to assist our customers in assessing and improving cybersecurity throughout their global supply chain.
- Supplier and sub-tier supplier cyber risk / vulnerability assessment, gap analysis, compliance audits
- Supplier cybersecurity capability development and training, cybersecurity implementation support
- Development / implementation of supply chain cybersecurity policies, processes, procedures, controls
- Cybersecurity consulting and advisory services, talent acquisition, staff augmentation
